Mobile Theft Prevention using Blockchain#
Industry Perspective
Key Insights
Mobile theft is a major concern for smartphone users worldwide, with an estimated 70 million smartphones lost each year.
Blockchain technology has the potential to provide a secure and decentralised solution to prevent mobile theft.
The proposed model of using blockchain for mobile theft prevention offers several potential advantages over existing methods, including decentralised and tamper-proof tracking, automation of processes, cross-border usage, and cost reduction.
The smart contract enables the registration of new mobile devices and maps them to their respective phone numbers. It provides a secure and tamper-proof solution for tracking the status of mobile devices on the blockchain.
The implementation of blockchain-based mobile theft prevention solutions provides an added layer of security that can greatly benefit mobile phone users, manufacturers, and society at large.
Introduction#
Mobile theft is a major concern for smartphone users worldwide. With the increasing reliance on mobile devices for personal and professional use, the theft or loss of a smartphone can result in a significant loss of data and privacy. Studies indicate that a staggering number of smartphones, estimated at 70 million, are lost each year, with a meagre 7% recovered [Hom16]. Further, company-issued smartphones are not immune to these occurrences, as research has shown that 4.3% of them are lost or stolen annually. Workplace and conference environments are the leading hotspots for smartphone theft, with 52% and 24% of devices stolen, respectively. Moreover, these numbers appear to be increasing, with recent studies indicating a rise of 39.2% between 2019 and 2021 [Hen22]. Given these alarming statistics, there is a growing need for effective mobile theft prevention measures. Blockchain technology has the potential to provide a secure and decentralised solution to prevent mobile theft. By leveraging the immutable and distributed nature of blockchain, it is possible to create a tamper-proof system that can prevent unauthorised access to mobile devices. In this article, we will explore the potential of blockchain technology for mobile theft prevention, its advantages and limitations, and the future prospects of this emerging field.
The proposed technology of using blockchain for mobile theft prevention is still in the development stage and has not yet been widely adopted on a national or international level. However, there are several companies and organisations that are exploring the use of blockchain for mobile security and anti-theft solutions. Internationally, companies such as Samsung and Huawei are researching the use of blockchain for mobile security, with Samsung filing several patents for blockchain-based mobile security solutions [For22, Hua18].
There is currently no known widespread adoption of blockchain for mobile theft prevention. However, governments all over the world have been exploring the use of blockchain for various applications, including supply chain management and digital identity. This indicates that there is an interest in the technology and a potential for the proposed model to be adopted globally.
Rationale Behind Mobile Theft Prevention Using Blockchain#
Mobile theft has become a growing concern for individuals and organisations around the world. In addition to the financial loss associated with the theft, there is also a significant risk of personal data being compromised. The use of blockchain technology for mobile theft prevention offers a secure and efficient solution for preventing mobile theft [Gob18]. This technology can help individuals and organisations protect their mobile devices and personal information by providing a decentralised and tamper-proof way to track and block stolen mobile devices. By using private blockchains, the proposed model can be implemented in a way that ensures security and privacy, while also reducing the risk of fraud or malicious activity.
Decentralised and tamper-proof: Blockchain technology enables a decentralised and tamper-proof system for tracking and disabling stolen mobile devices. This ensures that the information stored on the blockchain is accurate and cannot be tampered with, making it a reliable source for tracking stolen devices [Chi23].
Secure and private: The proposed model uses a private blockchain network that connects the mobile manufacturing companies and their nodes [Ire21]. This helps to ensure the security of the network and the data stored in it and helps to maintain the privacy of the users.
Automation of processes: Smart contracts can be programmed to automatically disable the device once the signal is sent, reducing human error and increasing efficiency [DD21].
Cross-border usage: The proposed model can be used in cross-border cases, making it more efficient and effective than existing methods [Ram21].
Cost reduction: By reducing the number of mobile thefts, the proposed model can also have a positive economic impact. This can include reducing the costs associated with mobile theft for consumers, mobile carriers, and insurance companies [Ali20].
Alternative Technologies Available under Development#
IMEI blocking: One of the most common methods for preventing mobile theft is to block the IMEI (International Mobile Equipment Identity) number of a stolen device. This can be done by reporting the theft to the mobile carrier, who will then blacklist the IMEI number and prevent the device from connecting to the network [Hic22].
SIM card blocking: Similar to IMEI blocking, SIM card blocking involves disabling the SIM card of a stolen device. This can be done by reporting the theft to the mobile carrier, who will then deactivate the SIM card and prevent the device from connecting to the network [Tre15].
Remote wipe: Some mobile devices include a remote wipe feature, which allows the device owner to remotely delete all of the data on their device if it is lost or stolen [AIT23].
Mobile tracking apps: There are a variety of mobile tracking apps available that allow device owners to track the location of their device and remotely lock or wipe it if it is lost or stolen [Mar23].
In comparison, the model of using blockchain for mobile theft prevention offers several potential advantages over these existing methods. A decentralised and tamper-proof system for tracking and disabling stolen devices, and the smart contract can be programmed to automatically disable the device once the signal is sent, reducing human error and increasing the efficiency. Additionally, the proposed model can potentially work in cross-border cases, which is not possible with IMEI and SIM card blocking, and also can be integrated with other theft prevention methods.
Methodology#
The smart contract enables the registration of new mobile devices and maps them to their respective phone numbers. This allows users to update the status of their mobile devices on the blockchain, indicating whether they are lost or stolen. The smart contract also allows for changes to be made to the registered mobile devices’ information, such as their International Mobile Equipment Identity (IMEI) number, and to update the corresponding phone number. In this way, the smart contract provides a secure and tamper-proof solution for tracking the status of mobile devices on the blockchain.
The mobile application is designed to constantly monitor the state of the mobile device by making API calls to the blockchain. If the blockchain indicates that the device has been reported stolen, the application acts by disabling the device’s Wi-Fi and network connections and forcing it into airplane mode. By doing so, the application prevents the thief from using any of the phone’s features, rendering it useless until it can be recovered by the rightful owner.
When a mobile phone is marked as stolen on the blockchain through the smart contract and later found, the owner can connect it to a computer via USB and use USB mode to provide data to the phone. This allows the owner to activate the phone again by providing the data through the USB-based hotspot.
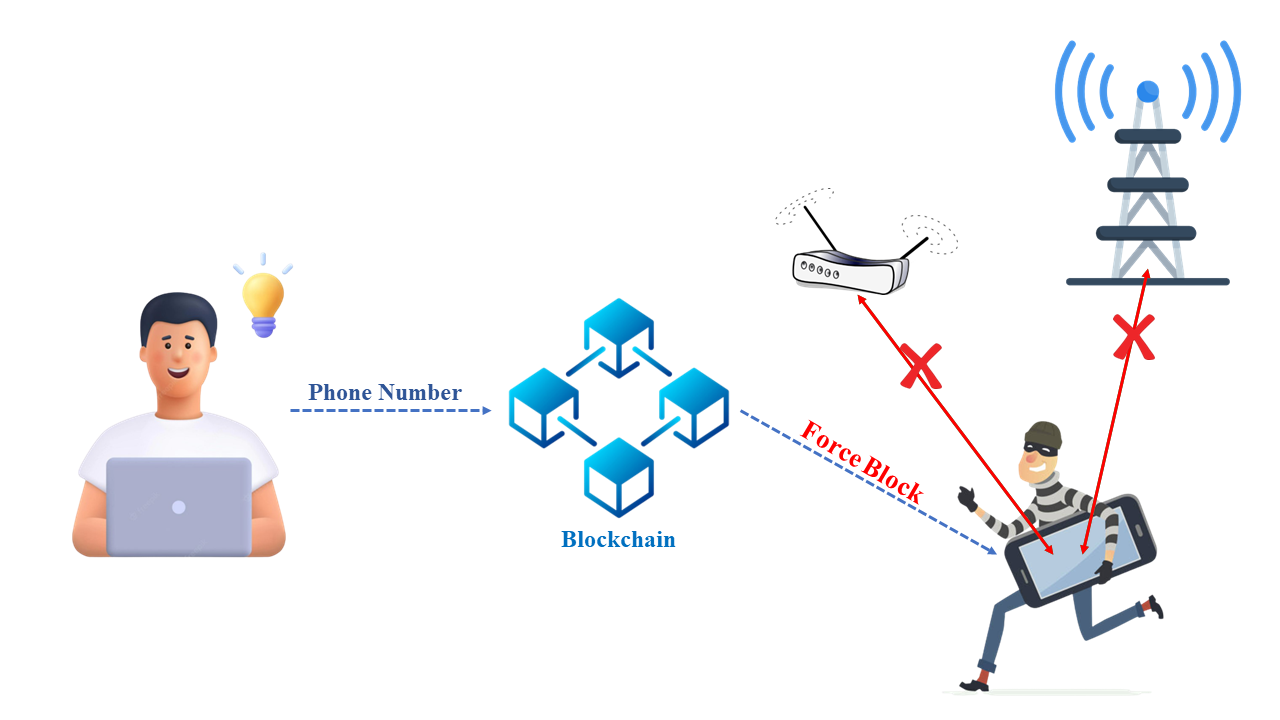
Fig. 21 Working Mechanism of Mobile Theft Prevention Using Blockchain#
The smart contract is written in both Solidity and JavaScript programming languages that can be deployed on a blockchain network. It is designed to prevent mobile theft by using a mapping function to keep track of mobile devices using their IMEI numbers and phone numbers.
The smart contract consists of six functions that can be called by authorised users.
addIMEI()allows users to add their mobile devices to the blockchain by passing in their IMEI and phone numbers. The function first checks if the IMEI and phone numbers already exist on the blockchain, and if not, it adds the device to the mapping function.activateLost()is used to activate the lost mode of a mobile device. The function checks if the IMEI number of the device exists on the blockchain and if it does, it sets the value ofisIMEIlostto true, indicating that the device is lost.deactivateLost()is used to deactivate the lost mode of a mobile device. The function checks if the IMEI number of the device exists on the blockchain and if it does, it sets the value ofisIMEIlostto false, indicating that the device is no longer lost.changeIMEI()allows users to change the IMEI number of their device. The function checks if the old IMEI and phone number exist on the blockchain and if it does, it replaces the old IMEI with the new one.changePhoneNumber()allows users to change the phone number associated with their device. The function checks if the old IMEI and phone number exist on the blockchain and if it does, it replaces the old phone number with the new one.checkIMEI()is a view function that allows anyone to check if a particular device is lost by passing in the IMEI number of the device. The function returns true if the device is lost, and false if it is not.
Impact on Users and Mobile Manufacturers#
As the world continues to advance technologically, mobile phone theft has become a common issue that affects many people. However, with the implementation of a blockchain-based mobile theft prevention solution, it is possible to mitigate this problem.
For users, this solution provides an added layer of security, ensuring that their mobile devices cannot be easily used if they are lost or stolen. With the mobile application continuously reading the state of the mobile through API calls to the blockchain, it is possible to detect if the mobile is stolen, and take appropriate actions to disable the mobile network, and Wi-Fi, and force activate airplane mode, preventing the thief from using any of the phone’s functionalities.
For mobile manufacturers, implementing blockchain-based mobile theft prevention solutions will increase customer satisfaction and retention as users are likely to be attracted by the added security feature. This, in turn, will lead to an increase in sales and profits.
Future Possibilities and Extensions#
The implementation of this blockchain-based mobile theft prevention solution has future possibilities and extensions. It can be extended to other mobile devices like laptops, tablets, and smartwatches, further increasing the level of security for users. Additionally, it can be integrated with existing law enforcement agencies to enhance the tracking of lost or stolen mobile devices. This will make it easier for law enforcement to recover stolen mobile devices and increase the likelihood of criminals being brought to justice.
In conclusion, the implementation of blockchain-based mobile theft prevention solutions provides an added layer of security that can greatly benefit mobile phone users, manufacturers, and society at large. The potential for future extensions and possibilities only adds to its value, making it an ideal solution for improving the safety and security of mobile devices.
References#
- Ali20
Ahmed Ali. Blockchain technology and business use-cases for cost reduction. pages, 12 2020.
- AIT23
Asha Iyengar, Jeff Borsecnik and Team. Perform a remote wipe on a mobile phone. Microsoft, 2023. URL: https://learn.microsoft.com/en-us/exchange/clients/exchange-activesync/remote-wipe?view=exchserver-2019.
- Chi23
Chirag. Blockchain: the technology revolutionizing mobile app security. Appinventive, 2023. URL: https://appinventiv.com/blog/blockchain-technology-revolutionizing-mobile-app-security/.
- DD21
Utpal Biswas Debashis Das, Sourav Banerjee. A secure vehicle theft detection framework using blockchain and smart contract. Springer, 2021. URL: https://doi.org/10.1007/s12083-020-01022-0.
- For22
Savannah Fortis. Samsung uses blockchain-based security for devices in its network. Cointelegraph, 2022. URL: https://cointelegraph.com/news/web3-protection-platform-introduces-improved-detection-mechanics-in-latest-update.
- Gob18
Andreas Göbel. Using blockchain to prevent mobile phone theft. Camelot, 2018. URL: https://blog.camelot-group.com/2018/12/using-blockchain-to-prevent-mobile-phone-theft/.
- Hen22
Beatriz Henriquez. Mobile theft and loss report - 2020/2021 edition. PREY Project, 2022. URL: https://preyproject.com/blog/mobile-theft-and-loss-report-2020-2021-edition.
- Hic22
Jacob Hicks. How to block a stolen iphone with an imei number. DeviceTests, 2022. URL: https://devicetests.com/how-to-block-a-stolen-iphone-with-an-imei-number.
- Hom16
Elaine J. Hom. Mobile device security: startling statistics on data loss and data breaches. ChannelProNetwork, 2016. URL: https://www.channelpronetwork.com/article/mobile-device-security-startling-statistics-data-loss-and-data-breaches.
- Hua18
Huawei. Huawei blockchain whitepaper. Huawei, 2018. URL: https://www.huaweicloud.com/content/dam/cloudbu-site/archive/hk/en-us/about/analyst-reports/images/4-201804-Huawei%20Blockchain%20Whitepaper-en.pdf.
- Ire21
Gwyneth Iredale. The rise of private blockchain technologies. 101 Blockchains, 2021. URL: https://101blockchains.com/private-blockchain/.
- Mar23
Karen Marcus. The 8 best phone tracker apps of 2023. Lifewire, 2023. URL: https://learn.microsoft.com/en-us/exchange/clients/exchange-activesync/remote-wipe?view=exchserver-2019.
- Ram21
Murali Ramakrishnan. How blockchain works in cross-border payments. Springer, 2021. URL: https://blogs.oracle.com/financialservices/post/how-blockchain-works-in-cross-border-payments-.
- Tre15
Mobile ICT Trends. Erasing your device, blocking your sim card: how to be prepared when your phone gets stolen. econocom, 2015. URL: https://blog.econocom.com/en/blog/what-to-do-if-your-mobile-device-gets-stolen-how-do-you-block-your-sim-card-heres-how-to-be-prepared-for-the-loss-or-theft-of-your-mobile/.
