Flash Loan Attacks in Decentralised Finance#
Industry Perspective
Key Insights
Flash loans, a distinct DeFi feature, offer uncollateralised loans within a single transaction, providing liquidity for various strategies. Flash loan attacks exploit DeFi vulnerabilities, aiming for high profits with minimal risk, resulting in substantial financial losses across multiple DeFi platforms.
Attackers use methods like oracle and governance manipulation, front running, and liquidity removal to exploit protocol vulnerabilities.
Notable flash loan attacks involve price oracles, governance manipulation, and liquidity drainage, showcasing the challenges in securing DeFi protocols.
Defensive strategies, such as transaction monitoring, requiring approval for flash loan usage, and improved oracle designs, aim to mitigate flash loan attacks. However, the evolving nature of attacks continues to challenge their effectiveness.
Ongoing research in monitoring, analytics, incentive mechanisms, and oracle designs is crucial to achieve stability in DeFi and maximise its potential. Security challenges persist due to the open and interconnected nature of DeFi protocols.
Introduction#
Decentralised finance (DeFi) seeks to replicate traditional financial services, such as lending and trading, using blockchain smart contracts. One notable feature is flash loans—uncollateralised loans that must be repaid within the same transaction [aav23]. Flash loans alleviate liquidity constraints for arbitrage and hedging strategies. However, they also equip potential attackers with capital for market manipulation.
In a flash loan attack, the borrower exploits vulnerabilities to extract profits exceeding the small loan fee. For instance, manipulating oracle prices to secure loans larger than what collateral would permit [aav23]. Flash loan attacks have resulted in over $750 million in losses across various DeFi platforms [DeF].
This science note reviews academic literature that analyses flash loan attacks in DeFi. First, we discuss attacker incentives and common methods. Next, we delve into prominent attack cases and their measurable impacts. Finally, we explore emerging defensive techniques and the remaining challenges. This examination highlights the novel risks posed by flash loans and the difficulties in balancing innovation and security in decentralised systems.
Flash loans leverage the atomicity of blockchain transactions — either all state changes succeed, or all are reverted. This ensures loan repayment before changes take effect [aav23]. Collateral is unnecessary since no counterparty risk is involved. Borrowers only need to pay a small fee (e.g., 0.09%) to the lending pool, making loans capital efficient. Lenders benefit from fee revenue, and borrowing demand boosts overall pool liquidity. However, attackers exploit the fact that flash loans provide almost unlimited capital for market manipulation within a single transaction. Successful attacks yield profits far exceeding the fractional loan fee.
Attack Incentives and Methods#
Flash lending made its debut in 2018 by the Marble Protocol and quickly found popularity with traders looking to profit off arbitrage opportunities between decentralised exchanges [aon]. The central incentive for flash loan attacks is to gain substantial profits with minimal risk. Attackers extract value from DeFi protocols before changes are reverted due to failed repayment. Importantly, there is essentially no cost to attempting attacks repeatedly as long as the initial loan is repaid [aav].
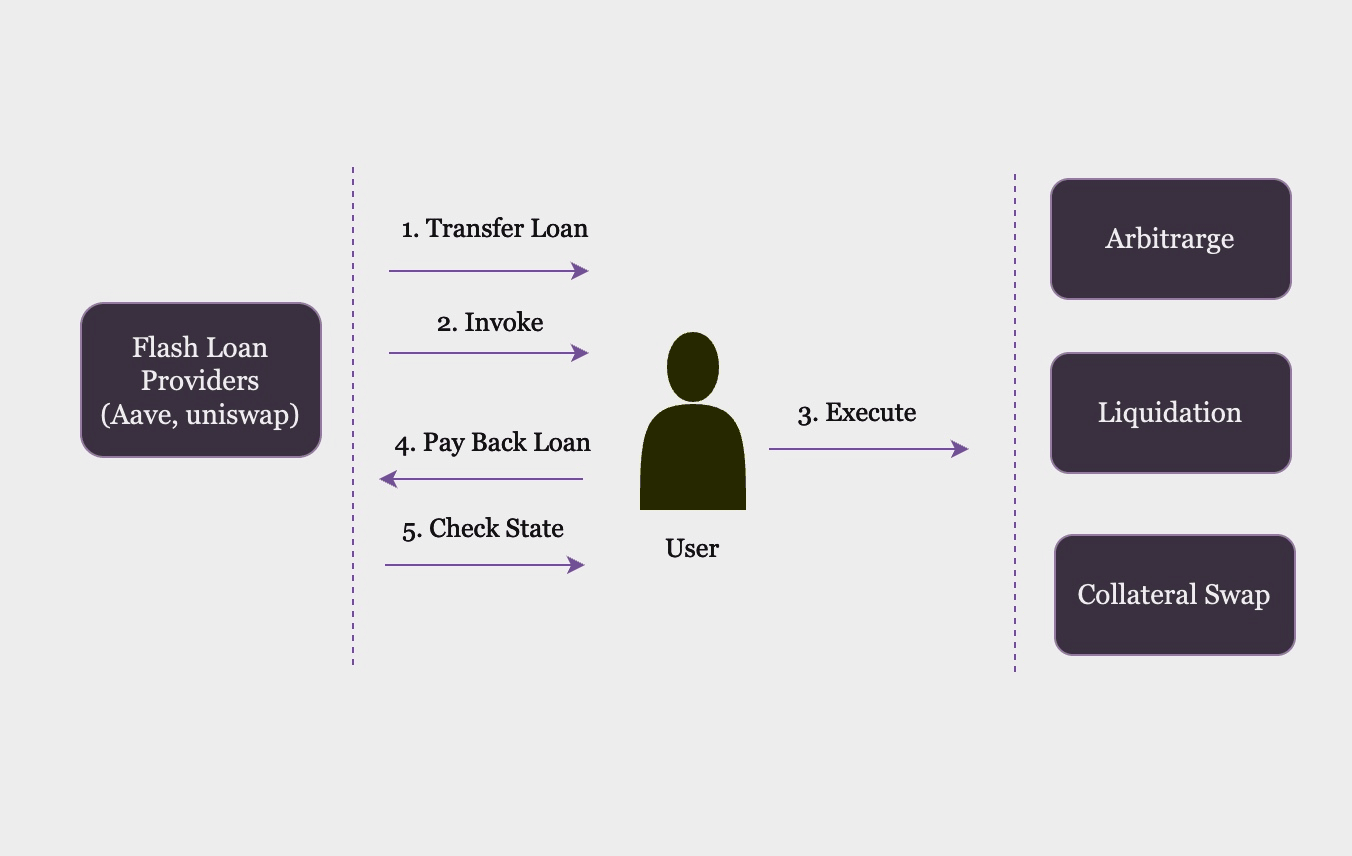
Fig. 9 Typical Flashloan Attack#
Typical attack methods include:
Arbitrage: Attackers can use flash loans to execute arbitrage transactions and profit from price differences between different decentralised exchanges (DEXs). Even though this attack may not be malevolent, reputable traders may nonetheless suffer losses as a result of it.
Price manipulation: Attackers can use flash loans to manipulate the price of a cryptocurrency by artificially inflating or deflating its value. This can cause significant losses for traders who have placed orders based on manipulated prices.
Removal of liquidity/Smart contract exploits: Draining pooled reserves through flash borrowing to disable markets or deposit contracts [WWL+21]. Attackers can exploit DeFi smart contract vulnerabilities including re-entrancy issues and integer overflow errors by using flash loans. They might be able to carry out more assaults or steal money from the protocol as a result [Pal].
These techniques combine borrowed capital with issues in incentive design, oracle integrity, and contract logic. Successful attacks across multiple protocols demonstrate how interconnectivity amplifies vulnerabilities [aav23].
Prominent Attack Cases#
Recent flash loan assaults have exposed the weaknesses and inherent risks of decentralised finance (DeFi) platforms. Euler Finance experienced a significant breach in March 2023, resulting in 197 million dollars in losses. The hacker was able to influence the platform’s borrowing capabilities by exploiting a weakness in Euler’s rate computation, notably within the eToken function. Similarly, Cream Finance had a flash loan attack in October 2021, resulting in losses of more than 130 million dollars. The attacker exploited flaws in Cream’s yUSDVault in order to double the perceived value of particular tokens. Furthermore, in November 2021, bZx was subjected to a sophisticated hack that included two independent assaults that targeted flaws in the platform’s reliance on a single oracle for pricing determination [Pal].
In total, 12 of the top 20 DeFi exploits by profit involved flash loans [DeF], with estimated losses exceeding $750 million. These incidents underscore how flash loans enable complex manipulation that is challenging to anticipate. Attacks are growing in sophistication by combining multiple techniques. These real-world cases emphasise the utmost importance of fortifying security measures, including the implementation of multiple trusted oracles and robust risk management protocols, to fortify DeFi platforms against flash loan attacks and curtail potential financial losses.
Emerging Defensive Techniques#
In response to rampant flash loan attacks, several defensive techniques have emerged. One approach involves transaction monitoring and the detection of common attack patterns, such as rapid pumping and dumping of oracles. This allows for pre-emptive action against the attack and transaction reversals.
Another mitigation strategy is to require credit-based approval for flash loan usage in a protocol’s smart contracts. While this restricts manipulation using flash loans, it may also compromise the intended flexibility of flash loans. Usage of models like the Recency, Frequency and Monetary model (RFM) which is a marketing technique used to quantify user value based on recency, frequency, and monetary value of purchases. Recency measures how recently a user has made a purchase, Frequency measures how often they purchase, and Monetary measures how much money they spend. Users are segmented into groups based on their RFM scores to identify reliable users.
At the protocol level, leveraging time-weighted average pricing via oracles helps reduce manipulation, as does using the maximum across multiple oracles. However, oracle designs remain a challenge. Additionally, proposals to share liquidity across central and decentralised exchanges can mitigate the impact of liquidity attacks [spr].
Despite these defences, the effectiveness remains elusive as attacks continue to grow more sophisticated. Inherent challenges persist in securing economic protocols atop public blockchains that permit open access [WWL+21].
Conclusion#
In summary, flash loans offer both capital efficiency and the potential for manipulation. Numerous DeFi protocols and users have fallen victim to sophisticated attacks, resulting in damages exceeding $750 million to date. Technical and economic solutions are still evolving, but following best practices like third-party auditing, re-entrancy guards and credit-based checks can mitigate the risks of such attacks immensely.
It is important to stay updated with the latest best practices and reports as the DeFi landscape is continuously evolving, by following best practices and being vigilant, we can help to build a safe DeFi landscape for everyone.
References#
- DeF(1,2)
De.Fi - DeFi Investing & Yield Farming Platform — de.fi. https://de.fi/incidents. [Accessed 30-12-2023].
- aon
Flash Loan Attacks: A Case Study | Aon — aon.com. https://www.aon.com/cyber-solutions/aon_cyber_labs/flash-loan-attacks-a-case-study/. [Accessed 30-12-2023].
- spr
Towards Secure and Trustworthy Flash Loans: A Blockchain-Based Trust Management Approach — link.springer.com. https://link.springer.com/chapter/10.1007/978-3-031-23020-2_28#Sec1. [Accessed 02-01-2024].
- aav23(1,2,3,4)
Flash Loans — docs.aave.com. 2023. [Accessed 30-12-2023]. URL: https://docs.aave.com/faq/flash-loans.
- aav
aavefoundation. Flash Loans: What Are They & How Do They Work? | CoinLedger — coinledger.io. https://coinledger.io/learn/flash-loans. [Accessed 30-12-2023].
- Pal(1,2)
Roman Palamarchuk. Flash Loan Attacks: Risks & Prevention - Hacken — hacken.io. https://hacken.io/discover/flash-loan-attacks/. [Accessed 02-01-2024].
- WWL+21(1,2)
Dabao Wang, Siwei Wu, Ziling Lin, Lei Wu, Xingliang Yuan, Yajin Zhou, Haoyu Wang, and Kui Ren. Towards a first step to understand flash loan and its applications in defi ecosystem. 2021. URL: https://doi.org/10.1145/3457977.3460301, doi:10.1145/3457977.3460301.
