Blockchain Bridge Security#
Academic Insight
Key Insights
To mitigate security risks, a cross-chain bridge that leverages zk-SNARK technology has been proposed. This provides a secure, trustless cross-chain bridge, marking the first implementation of Zero-Knowledge Proofs (ZKP) in a decentralised trustless bridge system.
To facilitate secure cross-chain interoperability, a Hash time-lock scheme that does not rely on external trust ensuring transaction security is introduced.
To mitigate token transfer risks, a series of protocols called TrustBoost using smart contracts to achieve a consensus on top of consensus mechanism is proposed.
In a bid to boost interoperability, a groundbreaking framework has been proposed that not only mitigates security risks inherent in cross-blockchain technology but also simplifies the process of identifying key assumptions and characteristics.
Introduction#
Blockchain technology has been lauded for its potential to disrupt various industries, given its unique properties such as decentralisation, transparency, and security. One recent advancement in this area is the development of blockchain bridges, which enable interoperability among different blockchains. Bridges facilitate communication between two blockchain ecosystems through the transfer of assets and information. However, as with any innovative technology, these bridges pose new security challenges. In this science note, we delve into the current academic landscape surrounding the security of blockchain bridges and summarise the recent research findings.
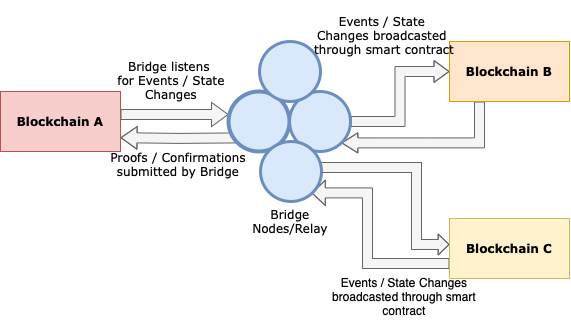
Fig. 20 Communication through a Blockchain Bridge.#
Interoperability and Security Challenges#
Interoperability in blockchain environments brings forth a series of unique security challenges. Trustless, interoperable, cryptocurrency-backed assets can be subjected to various threats. In April 2022, attackers were able to obtain five of the nine validator keys, through which they stole 624 million USD by exploiting the Ronin bridge, making it the largest attack in the history of DeFi [KY22]. According to blockchain analytics firm Chainalysis, until August 2022 recurring attacks against bridges have cost users around 1.4 billion USD [Bro22]. In 2022 attacks on bridges accounted for 69% of total funds stolen [Cha22].
This necessitates the development of novel security models and protocols to protect against potential attack vectors arising from cross-chain communication and is particularly true for blockchain bridges that need to uphold the integrity and security of transactions across disparate networks. Most existing solutions rely on the trust assumptions of committees, which lowers security significantly.
Xie et al. [XZC+22] proposed a solution by introducing zkBridge, an efficient cross-chain bridge that guarantees strong security without external trust assumptions. The main idea is to leverage zk-SNARK, which are succinct non-interactive proofs (arguments) of knowledge as a result security is ensured without relying on a committee. zkBridge uses the zk-SNARK protocol to achieve both reasonable proof generation times and on-chain verification costs. zkBridge is trustless as it does not require extra assumptions other than those of blockchains and underlying cryptographic protocols. It is the first to use Zero-Knowledge Proofs (ZKP) to enable a decentralised trustless bridge.
Pillai et al. [PBHouM22] proposed a novel cross-blockchain integration framework designed to guide the integration of cross-blockchain technology. The framework aids in identifying crucial assumptions and characteristics, mitigating security risks, enhancing the decision-making process, and minimising design mistakes and performance issues. It recognises the integration system as the fundamental unit of cross-blockchain technology, providing comprehensive analysis and addressing security concerns. Moreover, the framework supports businesses in designing and integrating various blockchain applications, while enabling a more accurate evaluation of security assumptions. Thus, it paves the way for effective interoperability among multiple blockchains.
The Role of Cryptography in Blockchain Bridge Security#
Securing blockchain bridges is greatly dependent on the strength of the cryptographic techniques deployed. The fundamental study by Kiayias et al. [KRDO17] on proof-of-stake blockchain protocols is of significant relevance. They outlined a novel cryptographic mechanism that provides transactional security while ensuring transparency.
To mitigate the reliance on external trust assumptions, Li et al. [LYY+23] in their paper proposed a Hash time-lock scheme that utilises a hash function and time-lock features to achieve cross-chain interoperability. The security of the Hash time-lock scheme is based on cryptographic hardness assumptions. The asset receiver is forced to determine the collection and produce proof of collection to the payer within the cut-off time, or the asset will be returned via hash-locks and blockchain time-locks. The proof of receipt can be used by the payer to acquire assets of equal value on the recipient’s blockchain or trigger other events. However, this scheme only supports monetary exchange and thus has low scalability.
Li et al. [LYY+23], identified a high-security and highly scalable option as the sidechains/relay scheme, which supports the interoperability of multiple objects such as assets and other data, thus having high scalability. In particular, the two-way peg is a mechanism that allows bidirectional communication between blockchains. An example of a two-way peg is simplified payment verification (SPV) in Bitcoin. Relays represent a mechanism that enables a blockchain network to authenticate data from other blockchain networks, eliminating the need for external third-party sources. Operating as a light client on a network, a relay system incorporates a smart contract and records block header information from different networks [F+20]. A trade-off of the sidechain implementation is that the vulnerability might increase in the main chain or other sidechains if there is a compromised sidechain in the network [Szt15].
Ding et al. [DDJ+18], proposed a framework for connecting multiple blockchain networks via an intermediary structure known as the InterChain. The InterChain possesses its own validation nodes, while SubChain networks are linked to this InterChain via gateway nodes.
Hardjono et al. [HLP19], discussed blockchain interoperability by drawing parallels with the design principles of Internet architecture. Just as the internet uses routers to guide message packets across its network at a mechanical level, they propose the use of gateways to direct messages between different blockchain networks.
Such cryptographic protocols can serve as a guiding light for the development of security measures in the context of blockchain bridges.
Scalability and Security#
As important as security is for blockchain bridges, it should not compromise the scalability of the systems. Zamyatin et al. [ZHL+19] discussed the scalability-security trade-off in their study on interoperable assets. There is a need for a balance that allows for scalability without jeopardising security. Future research in blockchain bridge security needs to address this delicate balance, ensuring the development of robust and efficient interoperable systems.
Zhang et al. [ZLZ20] introduced a method that facilitates asset exchange between inter-firm alliance chains and private chains. Users from both the sending and receiving chains authenticate their identities and secure a certificate by interacting with the alliance chain. When a cross-blockchain transfer request is initiated, the alliance chain validates the ownership of the users over the assets, and then proceeds with the asset transfer through a cross-blockchain interaction process.
Maintaining Sovereignty of blockchains#
Existing solutions to boost trust using a stronger blockchain, e.g., via checkpointing, require the weaker blockchain to give up sovereignty. Wang et al. [WSK+22] in their paper present a series of protocols known as TrustBoost designed to bolster trust across multiple blockchains without compromising their sovereignty. These protocols function through smart contracts, achieving a “consensus on top of consensus” that avoids changes to the blockchains’ consensus layers. TrustBoost operates by allowing cross-chain communication via bridges, facilitating the sharing of information across smart contracts on different blockchains. This system maintains its security as long as two-thirds of the participating blockchains are secure. Furthermore, TrustBoost shows potential in mitigating risks associated with cross-chain token transfers and exhibits promising prospects for future applications, especially as heterogeneous blockchain networks continue to mature.
Conclusion#
Blockchain bridges represent an important evolution in blockchain technology, facilitating crucial interoperability. However, the security aspects of these bridges are complex and multifaceted, requiring rigorous academic and industry attention. The body of research surrounding blockchain security provides critical insights that can help guide the development of secure and efficient blockchain bridges. As this field continues to evolve, a focus on understanding and mitigating security risks while maintaining scalability will be paramount.
References#
- Bro22
Ryan Browne. Hackers have stolen $1.4 billion this year using crypto bridges. here’s why it’s happening, cnbc. CNBC, 2022. URL: https://www.cnbc.com/2022/08/10/hackers-have-stolen-1point4-billion-this-year-using-crypto-bridges.html.
- Cha22
ChainAnalysis. Cross-chain bridge hacks emerge as top security risk, chainalysis. ChainAnalysis, 2022. URL: https://blog.chainalysis.com/reports/cross-chain-bridge-hacks-2022/.
- DDJ+18
Donghui Ding, Tiantian Duan, Linpeng Jia, Kang Li, Zhongcheng Li, and Yi Sun. Interchain: a framework to support blockchain interoperability. Second Asia-Pacific Work. Netw, 2018.
- F+20
P Frauenthaler and others. Leveraging blockchain relays for cross-chain token transfers. 2020. URL: https://www. dsg. tuwien. ac. at/projects/tast/pub/tast-white-paper-8. pdf. White Paper, Technische Universität Wien. Version, 2020.
- HLP19
Thomas Hardjono, Alexander Lipton, and Alex Pentland. Toward an interoperability architecture for blockchain autonomous systems. IEEE Transactions on Engineering Management, 67(4):1298–1309, 2019.
- KY22
Sam Kessler and Sage D. Young. Ronin attack shows cross-chain crypto is a bridge too far, coindesk latest headlines. CoinDesk, 2022. URL: https://www.coindesk.com/layer2/2022/04/05/ronin-attack-shows-cross-chain-crypto-is-a-bridge-too-far/.
- KRDO17
Aggelos Kiayias, Alexander Russell, Bernardo David, and Roman Oliynykov. Ouroboros: a provably secure proof-of-stake blockchain protocol. In Advances in Cryptology–CRYPTO 2017: 37th Annual International Cryptology Conference, Santa Barbara, CA, USA, August 20–24, 2017, Proceedings, Part I, 357–388. Springer, 2017.
- LYY+23(1,2)
Taotao Li, Changlin Yang, Qinglin Yang, Siqi Zhou, Huawei Huang, and Zibin Zheng. Metaopera: a cross-metaverse interoperability protocol. arXiv preprint arXiv:2302.01600, 2023.
- PBHouM22
Babu Pillai, Kamanashis Biswas, Zhé Hóu, and Vallipuram Muthukkumarasamy. Cross-blockchain technology: integration framework and security assumptions. IEEE Access, 10:41239–41259, 2022.
- Szt15
Paul Sztorc. Drivechain-the simple two way peg. 2015.
- WSK+22
Xuechao Wang, Peiyao Sheng, Sreeram Kannan, Kartik Nayak, and Pramod Viswanath. Trustboost: boosting trust among interoperable blockchains. arXiv preprint arXiv:2210.11571, 2022.
- XZC+22
Tiancheng Xie, Jiaheng Zhang, Zerui Cheng, Fan Zhang, Yupeng Zhang, Yongzheng Jia, Dan Boneh, and Dawn Song. Zkbridge: trustless cross-chain bridges made practical. arXiv preprint arXiv:2210.00264, 2022.
- ZHL+19
Alexei Zamyatin, Dominik Harz, Joshua Lind, Panayiotis Panayiotou, Arthur Gervais, and William Knottenbelt. Xclaim: trustless, interoperable, cryptocurrency-backed assets. In 2019 IEEE Symposium on Security and Privacy (SP), 193–210. IEEE, 2019.
- ZLZ20
Jianbiao Zhang, Yanhui Liu, and Zhaoqian Zhang. Research on cross-chain technology architecture system based on blockchain. In Communications, Signal Processing, and Systems: Proceedings of the 8th International Conference on Communications, Signal Processing, and Systems 8th, 2609–2617. Springer, 2020.
